Services
In addition to the computers we provide for your use, several additional services are available to you.
Service Passwords
Services that require you to authenticate ask for you password. For some of those services like email it is very common to use the save password function of your email client. This can be a security risk since very often that software uses weak or no encryption and a compromised password not only allows acces to that one service but to all of your files and services.
Therefore we strongly recommend setting separate passwords for those services:
- Use
cip-set-password -lto view a list of services you can set separate passwords for. - With
cip-set-password -s mail -ryou can remove the password for the email service.
In all those cases you will be asked for your main account password before any access or change is made. When a service password is set, access to that service is possible via your main account password and the service password for that service. If you should lose a password, please remember that changing your main account password does not change any service passwords. You will need to change or remove them separately.
Remote Login - via SSH
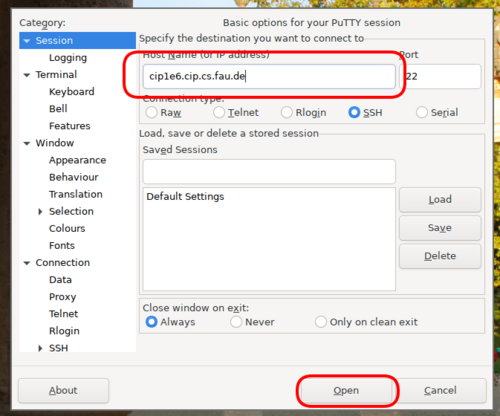
All our machines have SSH enabled. You can login from Linux with the command
ssh yourloginname@hostname.
To login from a Windows system you'll need to install a SSH-Client, e.g.
Putty.
On some hosts (cip2a7, cip2a0, cip1a0, cip1c6, cipterm0, ircbox) SSH additionally listens on port 443 in order to make connecting from networks with restrictive firewalls easier.
The hosts cip2a[0-7], cip2b[0-2], cip2c[0-2], cip2d[0-2], cip2e[0-2], cip2g[3-7], cip1e[0-7], cip4* and all the terminal servers (cipterm0, ircbox) are always online, all others are shut down during the nights (20:00 - 08:00), on weekends, and during the term holidays. The available hardware is listed in the Room Index.
Authenticating hosts
There is a list of all SSH host keys to verify the authenticity of the connection.
Alternatively, if you're using OpenSSH (you probably are unless you're on
Windows), you can trust our SSH certificate authority by adding the following
(quite long) line to your ~/.ssh/known_hosts file:
@cert-authority *.cip.cs.fau.de,faui0*.cs.fau.de,faui0*.informatik.uni-erlangen.de,ircbox.cs.fau.de,ircbox.informatik.uni-erlangen.de,gitlab.cs.fau.de ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPmZxYAdJDYgQOrfht7VAeb5Kk/ZFldwTvA4H7jGyABx problems@cip.cs.fau.de
Since all our host keys are signed by this CA, you then shouldn't ever have to verify one of our hosts again.
We also publish fingerprints in SSHFP DNS records. Trusting these is only secure if have a trustworthy DNSSEC-validating DNS resolver and the network between you and said resolver is equally trustworthy. Usually this means you're running your own local resolver. Telling your ssh client to trust these records is left as an exercise in reading man pages.
Remote Login - with grapical interface via Xpra
This tutorial has its separate webpage.
Installation and requests
More information about using and installing Xpra with native clients can be found on the Xpra homepage.
If you need another application for a course, which is not available like this, you can request it by e-mail.
GitLab
We offer a local instance of the git-based collaboration platform GitLab.
Here is an FAQ regarding access and usage of GitLab. There is also a howto on how to keep your repositories binary data free.
VPN
Encrypted remote access to the university network is from now on available at the RRZE. Previous assigned alternatives remain active for now.
Homepage
Files in the directory ~/.www/ are exported at the web address
https://wwwcip.informatik.uni-erlangen.de/~yourloginname.
For this to work the user www must have access to these file.
To create a preconfigured Homepage, the cip-mkhomepg command can be used.
These pages are publicly available! Authentication can be added using Kerberos.
Commercial usage of any kind, such as advertisement for a company, endorsement of commercial software etc. is prohibited!
Every user has an email address <loginname>@cip.cs.fau.de.
You can forward incoming mail to another address by writing the desired
destination into the file ~/.forward. The change is active immediately.
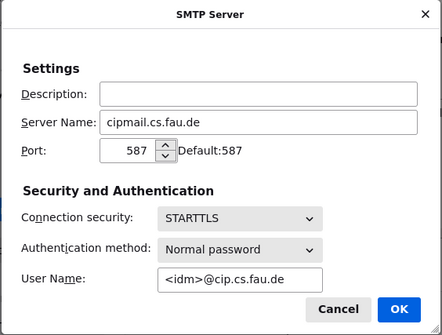
In order to access your mail via IMAP, first you have to run a command like
mkdir -p ~/Maildir/{cur,new,tmp} && chmod 700 ~/Maildir/{,cur,new,tmp} to
create and secure your maildir. Then write a line containing only the
characters ~/Maildir/ into the file ~/.forward. This redirects incoming mail
to the directory Maildir in your home, where the IMAP server is looking for
it.
Now you can point your mail client to port 993 on
cipimap.informatik.uni-erlangen.de.
You can set a password using the command cip-set-password -s mail or use your
existing login password.